Curriculum
∎ A new advanced track with 18 to 21 credits for each major in different departments
∎ Compactness of credits for Experiment courses and majors
- Experiment Course (14 -> 6 credits)
- Major Course ( 72 -> 63 credits)
∎ Upgraded major core credits by further classifying artificial intelligence-related Courses into major cores ( 27 -> 36 credits)
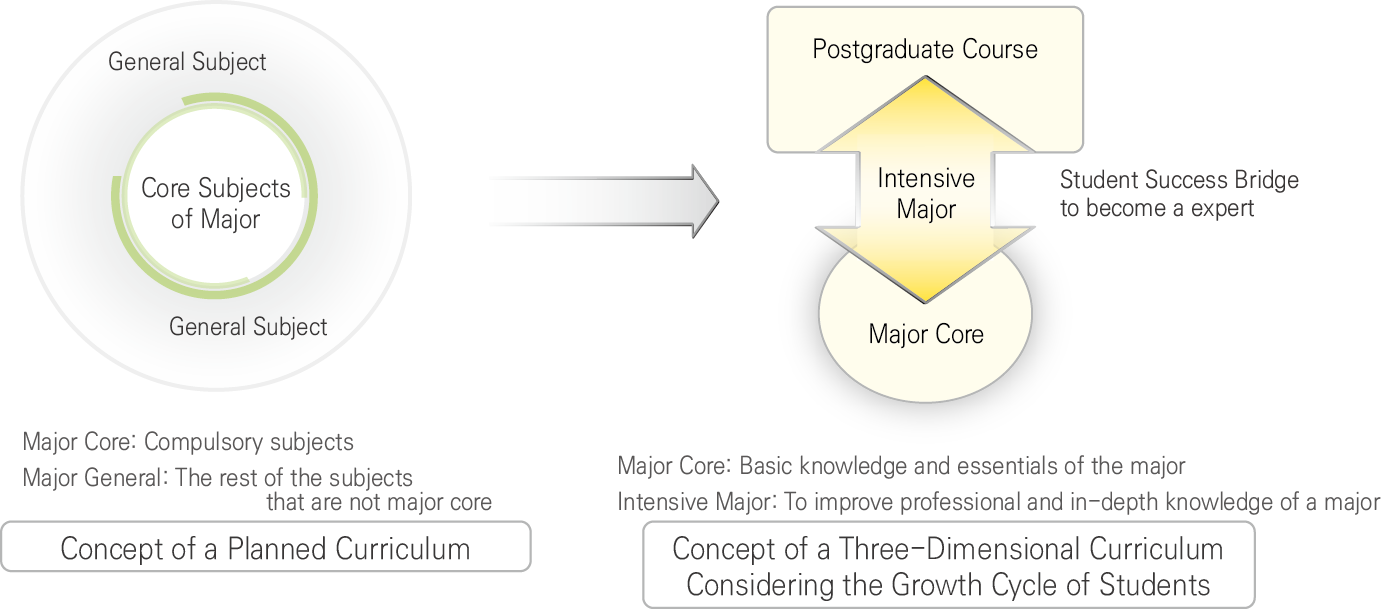
∎ Eliminating existing major core / general distinction and reorganizing into problem-solving and TOPIC-centered major core and depth courses
∎ Major Core Tracks for Undergraduate and Graduate General Courses
| Course | Education Contents | Category |
|---|---|---|
| Distributed Computing Principle | The latest theories of distributed systems | 3 Credits |
| Blockchain and Smart Contracts | The latest technologies and theories of blockchain | |
| Artificial Intelligence Security | The latest security technology utilizing Artificial Intelligence | |
| Information Visualization | The latest theories and technologies of Information Visualization | |
| Software Structural Design Theory | Analyze the latest computer architecture | |
| Compilers and Principles of Language | The latest compiler and programming language design | |
| Network Artificial Intelligence | The latest network technology leveraging AI | |
| Advanced Computer Network Design | Latest theory of Advanced Computer Network | |
| Virtual Reality | Foundation and latest technologies of Virtual Reality | |
| Robot vision | (Information and Communiation Technology) 4th Industrial Convergence Subject | |
| U-Healthcare | (IT Convergence) 4th Industrial Convergence Subject | |
| Intelligence Control | (ECE) 4th Industrial Convergence Subject |




